
IP Traceback Problem: How do we determine where malicious packet came from ? It's a problem because attacker can spoof source IP address If we know where. - ppt download

Intrusion Detection and IP Traceback Schemes for Cybersecurity: Pynbianglut, Hadem: 9798889952800: Amazon.com: Books

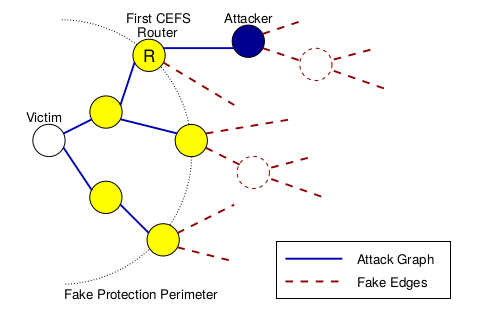












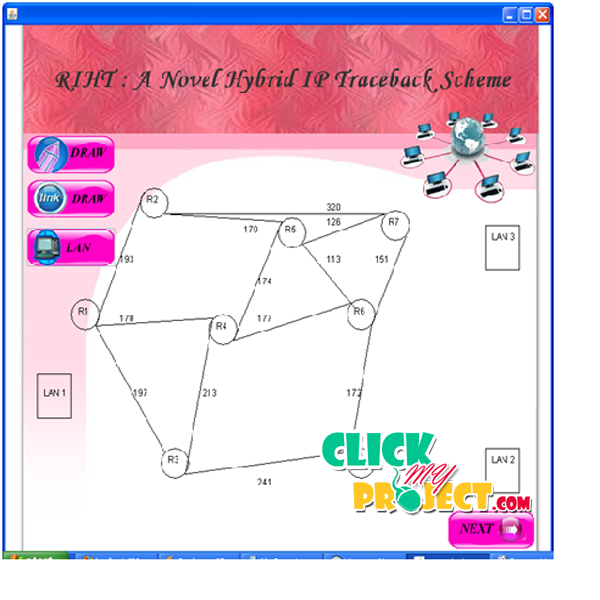



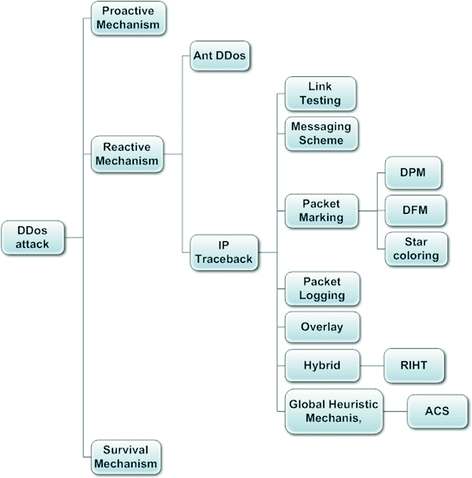

![PDF] A Brief Survey of IP Traceback Methodologies | Semantic Scholar PDF] A Brief Survey of IP Traceback Methodologies | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/116faf5d8b7345046148d79007250382c73c4edb/3-Figure1-1.png)

